Disk Analysis
For this challenge, we have a zip file containing a ReadMe.md and a suspectDisk.raw. The ReadMe.md file tells us:
1
2
#Context
Our informations are that a flag is hidden on this disk. However, we have trouble finding it. Can you help us ?
Setup
First of all, we need to create a mounting point so that we can mount the raw file on it and being able to read its content. I did the following:
1
2
3
sudo losetup -f --show ./suspectDisk.raw
sudo mkdir /mnt/THCon23
sudo mount /dev/loop0 /mnt/THCon23
The first command returned
/dev/loop0so this is what I used in the last one.
Recover Deleted Files [ TestDisk ]
Now we need to use TestDisk to read the content of the raw file we just mounted. Just run testdisk and select No Logs.
Now you can select your mounted device.
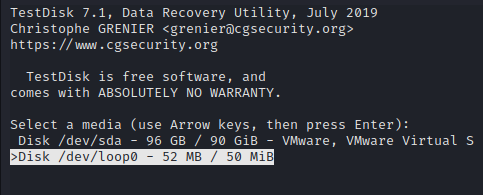
Then we can select None.
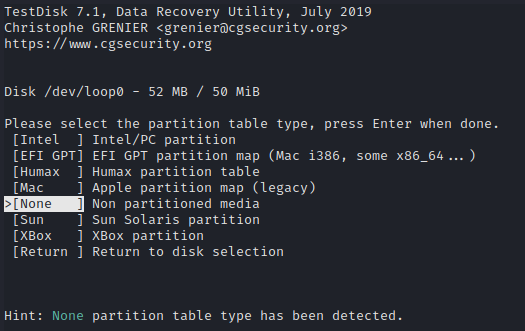
We can see at the bottom that
TestDiskadvise us to useNone.
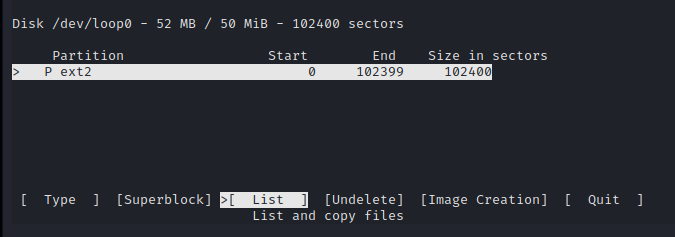
We can now list the content of the mounted device:
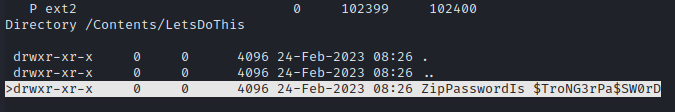
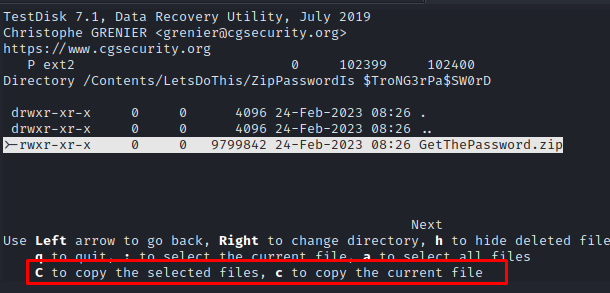
In the Content directory we can see that there is a LetsDoIt folder that was deleted. We can list its content and we find a folder with the password of the zip it contains:
We can now download the zip file using the capital C on it:
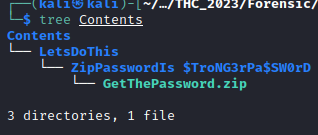
You can select any folder where you want to save it. I choosed the root folder of my working directory. As we can see, the file was saved using the same tree structure:
Finding the flag
When looking at the tree structure of the zip file once unzipped…
We can look for a file with “flag” in it:
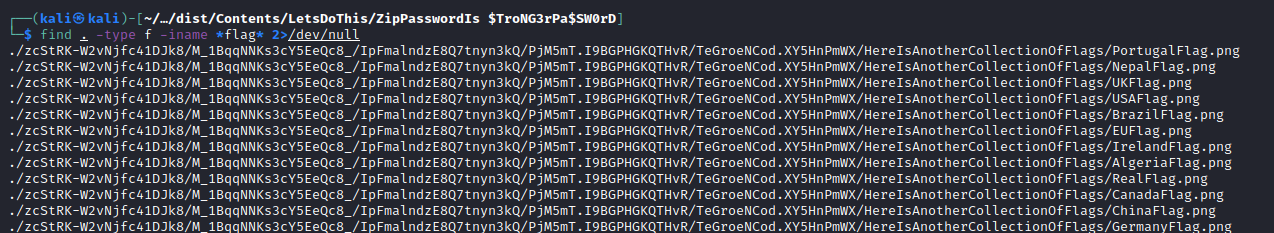
Well…There are a few… I tried to look if there were a folder or a file with a specific name like .txt file or a file that isn’t a .png file but didn’t find anything. I then wondered… “How is the chall created ???” and I thought that the tree structured was created with all the shitty images and then the flag was put in a specific folder. I then tried to look for the last modified file and:
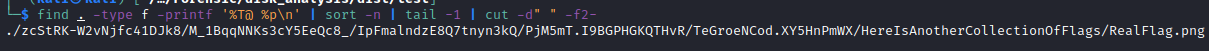
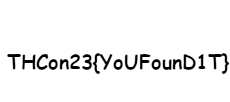
To remove the created folder and the mounted device you can use the following commands:
sudo umount /mnt/disk_thconandsudo losetup -d /dev/loop0.