LazySysAdmin #2
In this challenge, we are given an .iso file. We can mount it on our machine and see the root folder of a Linux machine:
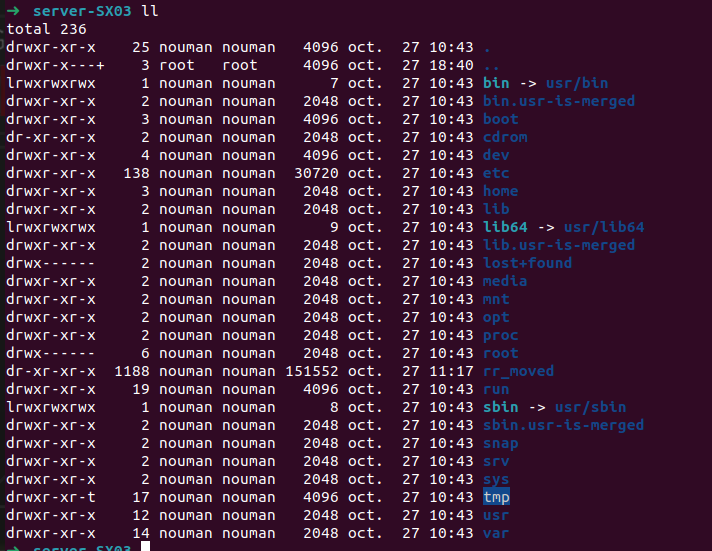
First I tried to look inside the rr_moved folder but there was nothing in it. The next guess I had was to look inside the /tmp folder because it’s where we upload usually our stuff as attackers:
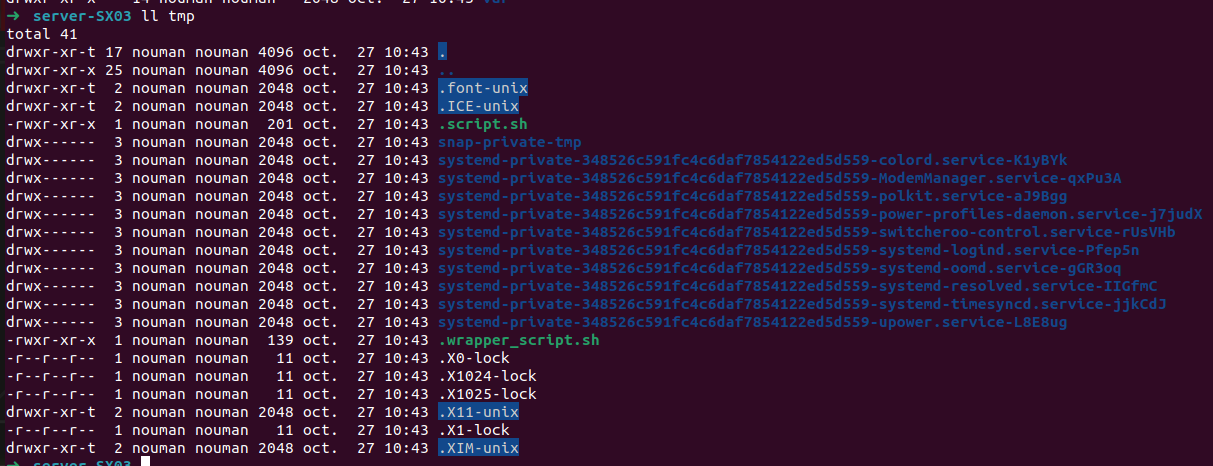
We see two hidden files, .script.sh and .wrapper_script.sh:
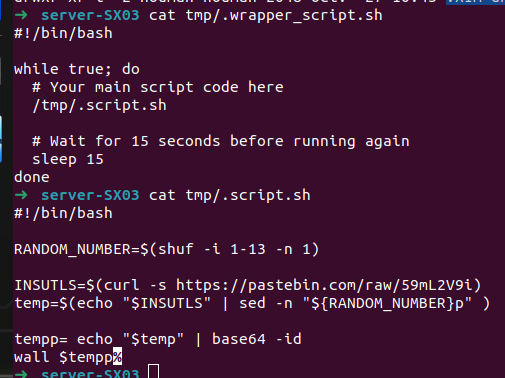
As we can see, the first script only run the second one and the second one recover strings from an URL. Lets curl the URL:
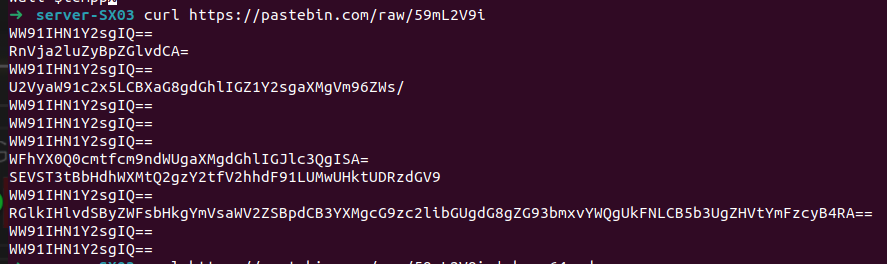
As we can see, there is a bunch of base64, lets decode it:
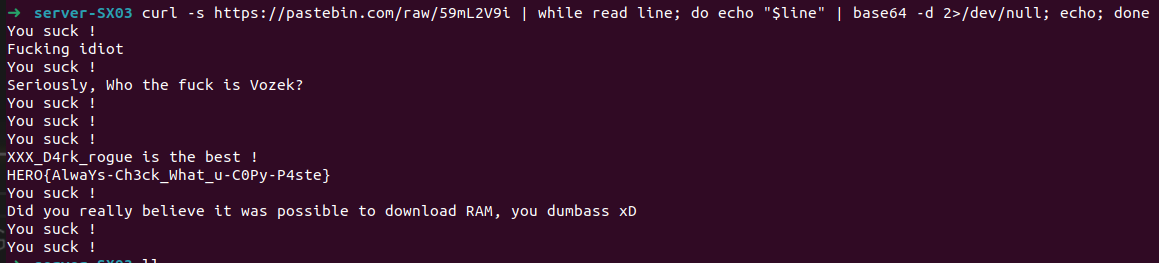
And… Voila. We get the flag HERO{AlwaYs-Ch3ck_What_u-C0Py-P4ste}