Hackbook Bonus
For this chall, we needed to create an account on a website called Hackbook. When we access the website we can notice that there are a lot of posts. At first I tried to download the images but when I saved them, it was in WEBP format. So it was not possible to use classic steganography tools. I looked at the URL to find where the original image was stored. After a few attempts on several images, I try to look somewhere else and began to lose myself in the website, on the github of some user and on the Instagram of another. I didn’t miss any Rick Roll I believe. But then came back to the original website. There was an image that caught my attention at the beginning.
Getting the flag
The interesting image was this one:
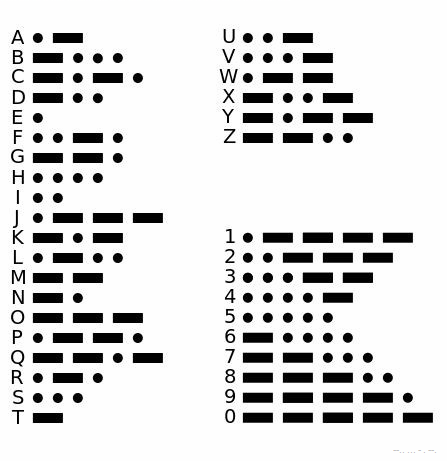
I noticed that at the bottom there is a Morse code but… DVR don’t seem to be a flag… I put the image on Aperisolve and found an interesting Morse string at the top:
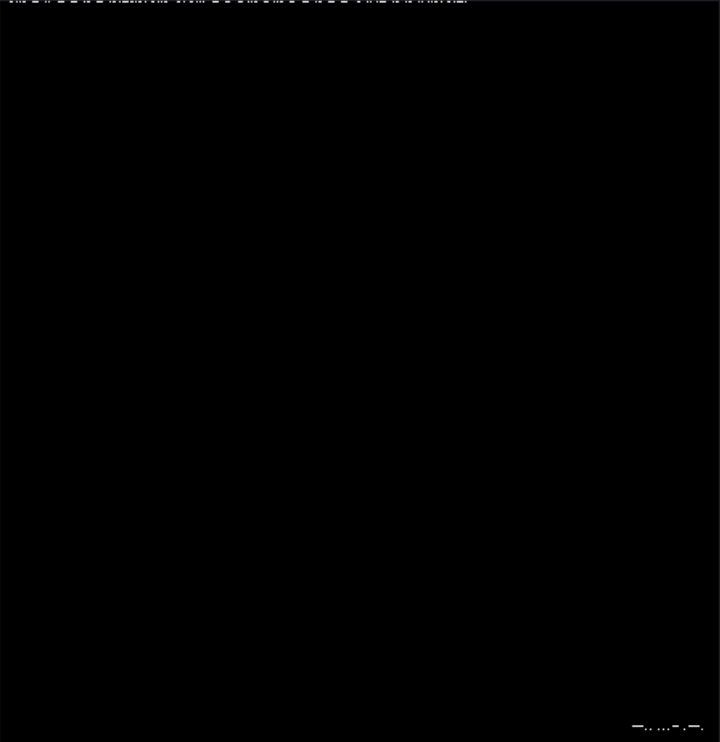
The Morse code wasn’t
DVRbutZSTEG(my mistake :) ). It was in fact--.. ... - . --.(I missed a space and some double dash). So obviously we should use Zsteg
But I believe that TUTITTATAETUTETSTTTUTUTTATTTIAAAIUETR isn’t a correct flag… I then found in the Zsteg output some interesting string:

We can find the flag thanks to the dcode website:
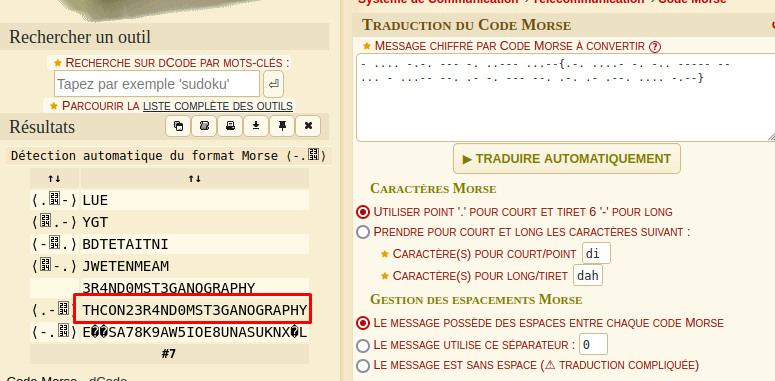
We don’t forget to add the curly bracket and… Voilà THCON23{R4ND0MST3GANOGRAPHY}