Ransomémoire
In this chall of forensic, we are given a 2Gb memory dump of a windows machine. To analyse a memory dump, a geat tool is Volatility. In this chall, we coulnd’t use Volatility2 so we needed to use the version 3. I found a good blog about the conversion of the Volatility2 to 3 commands (there are only the main ones, but still interesting).
We used the sessions command to find all the information we want (user, machine name and browser). The full command is volatility3/vol.py -f fcsc.dmp windows.sessions:
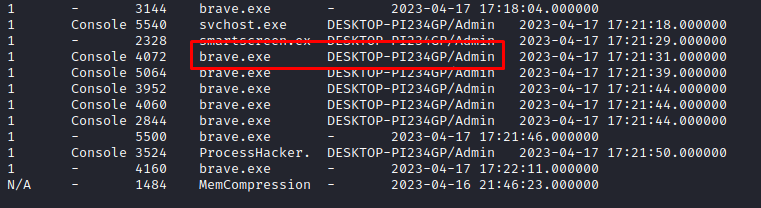
We have here everything we need to craft the flag: FCSC{Admin:DESKTOP-PI234GP:brave}.