Aaarg
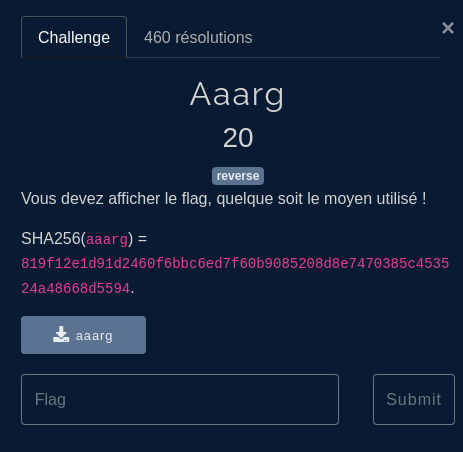
This chall is a reverse chall. When looking at the executable in Ghydra, we can see what looks like a flag in the .rodata section:
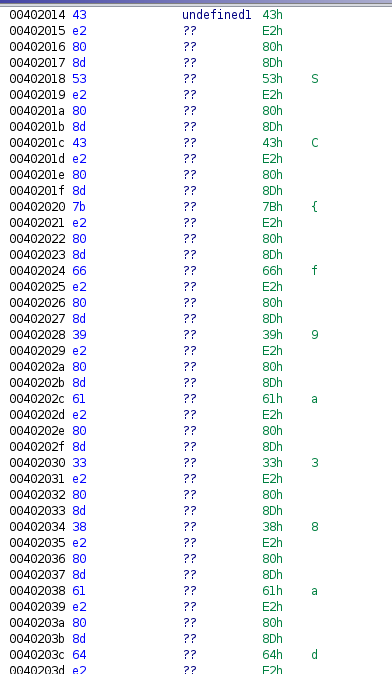
We then use r2. We use aaa to analyse the executable. We see a the address of .rodata using the iS command:
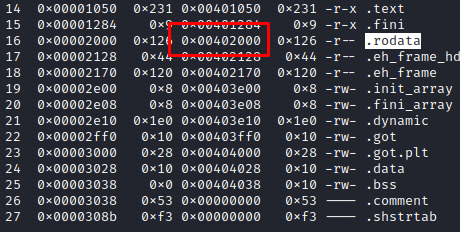
We then seek for the address of .rodata we just found and we can find the flag:
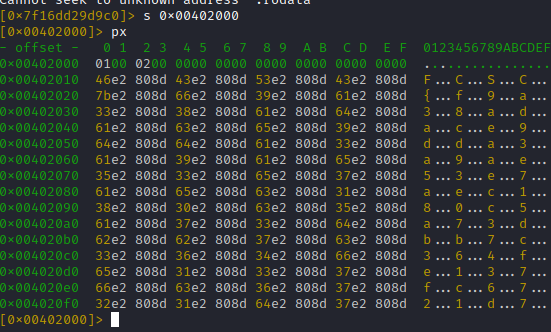
We can use the plx 20 command to read more and get the full flag:
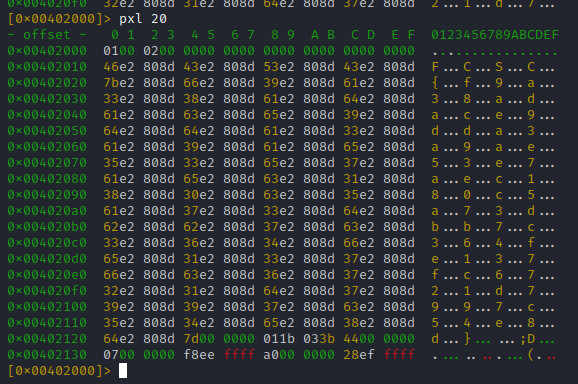
The full flag is FCSC{f9a38adace9dda3a9ae53e7aec180c5a73dbb7c364fe137fc6721d7997c54e8d}.