Introduction
To be able to participate in the Side Quest challenge, we had to find the URLs to the different challenges:
First QR Code
The first one is, as specified earlier, on their social media. On the Advent Of Cyber 2023 they give us the list of their social media:
I chose to start by LinkedIn and continue in order. So to find it on LinkedIn, I search for all the posts from TryHackMe and found this one:
We click on the link and get the first QR Code.
Discord
The Discord QR code was easy to find, we just had to search the pinned images on the Side Quest channel of the Discord. We find the following:
This gives us the link to the QR Code. The link to the message is here.
Going on Twitter, we find the following post:
We get the link to the 3rd QR Code.
Side Quest
The last QR Code was free. Indeed, we just had to head to the Side Quest page and we find it lying around:
I then downloaded all of them and created a python script (available here) to merge them together and to read it. We then get the following result:
We now have access to the first Side Quest at https://tryhackme.com/jr/adv3nt0fdbopsjcap
You can see the write up of this challenge here
Second QR Code
The second one was the harder to get I believe. At the end of the 6th day of the Advent of Cyber we can see this:
This task was about an introduction to buffer overflow. Even if this is a pretty complex attack, they managed to make it simple and fun.
Let’s get back to our initial goal. We need to find the QR Code. In a glitch ??? I didn’t understand what I was looking for…
To sum up, in this challenge, we can modify our name. But all the variables are following each other:
So if we have a name longer than 12 characters, we can specify values for the other variables.
To start, we need to earn some cash. We can hit the computer 16 times and specify a 16 long name:
As we can see, we paid one coin for each letter and we now have the name AAAAAAAAAAAAAAAA and we have 1094795585 coin. That’s great. Now we can go to the store and buy whatever we want:
As we can see, the IDs of each product is an hexadecimal character. So what if we have the items from 0 to f ? As we saw earlier on the second image of this part, the items are at the end of the memory. We need to right 4*11 (44) characters (as a padding) and then specify our items.
So let’s specify our name as 44 A’s and then right the string 0123456789abcdef to see what whe get:
When we press enter, we get the following items:
The value 0 wasn’t an item but every other hexadecimal value was an item and we got them all !!!
When we go to the tree and interact with it we can see all our items on it:
This only gives us the flag… Not the QR Code… I decided to find a glitch on the gates or on the house but couldn’t find anything… I then decided to head back to the merchant:
If you can see, he tells us that I have the yeti’s badge, but the correct one is blue… I can buy it to him. When we skip the dialogue, we get directly to the store. We can imagine that with the right amount of money we could pay for the yeti’s badge instantly. Let’s get some money :) We started with a bunch of As, I changed to replace all the As by some Zs but it wasn’t enough. I decided to check on the ASCII table to search for a greater value than Z:
To see the ASCII table from your terminal on Linux, run the command
man ascii.
As we can see, the } character gives us a good chance to get enough money. So with 16 } and I got 2105376125 coins:
I first had to empty my inventory because it was full and then bought the item with the ID a:
As you can see on the images, there is a new character. Is it… The GLITCH ???
This looked like a riddle at first… So we understand that we need to change our name as Snowball (because we have the cat character), we need to set the merchant name to Midas and the name changer’s name to Ted. We also need exactly 31337 coin and to do the 30 lives secret…
So obviously, because each variable are following each other, we need to first change the name changer’s name, then the merchant one, then the coin and finally our name.
So we can use just a padding of 28 As followed by Ted:
As we can see, the name changed to Ted. We now need to do the same for Midas with a padding of 16 As:
We now need to specify the coin value to 31337. But we need to be careful because by setting our name to Snowball we will use 8 coins. So we need to specify an amount of 31337+8 which is 31345. But 31345 is a decimal value. We need to change it to hexadecimal and finally to text so we can enter this text value after the padding:
So we need to change the value of 7A71 as a text and put it after our padding and it should be ok. So the text value is zq:
But we still have a A at the end that is changing the value of our coin wallet. Let’s set first zqA and after that the last bit is also None we will put zq:
Uhhh wait… We have 29050 but we should have 31345 ??? Oh wait, this is because zq <=> 7A71 and 29050 <=> 717A… This means that we need to put qz instead of zq to have 31345 coins:
Let’s now change our name to Snowball:
As we can see, we have 31337 coins as asked by the glitch ;)
We now need to do something regarding the 30 lives secret… I didn’t know what that means so I typed it on my search engine and found this Wikipedia page. It is in fact the Konami Code. This is a well-known cheat code for many gamers:
So I went to the glitch and used my arrow keys to do the Konami Code and then pressed B followed by A:
After a bit of waiting, I finally see the Yeti:
I go to speak with him and I get the QR Code:
The final URL is https://tryhackme.com/room/armageddon2r
Third QR Code
On the 12th day, we can see this at the bottom of the page:
We finish the task and get a vansprinkles session using the Pass The Hash (PtH) technique:
We see that there is something that looks like a website, we download everything using the download function in evil-winrm:
With our Python server on port 8000 we can look at the webpage chatlog.html:
It looks like a save of a chat. As we can see, there is a message that has been deleted and then the original message was sent but cropped with the information we, I believe, need:
So I recovered the cropped image called Screenshot 2023-11-22 034941.png. I know from this CTF that we can recover the content of a cropped image. So I use Acropalypse-Multi-Tool:
If you want a better understanding of why this works, I advise you to check my WU on the 404 CTF
We first need to know the original size. This can be done by looking at the first screenshot of the desktop:
Now we know that the image is 2560 x 1080, so I ran the tool on my image and found the QR Code:
The final image is :
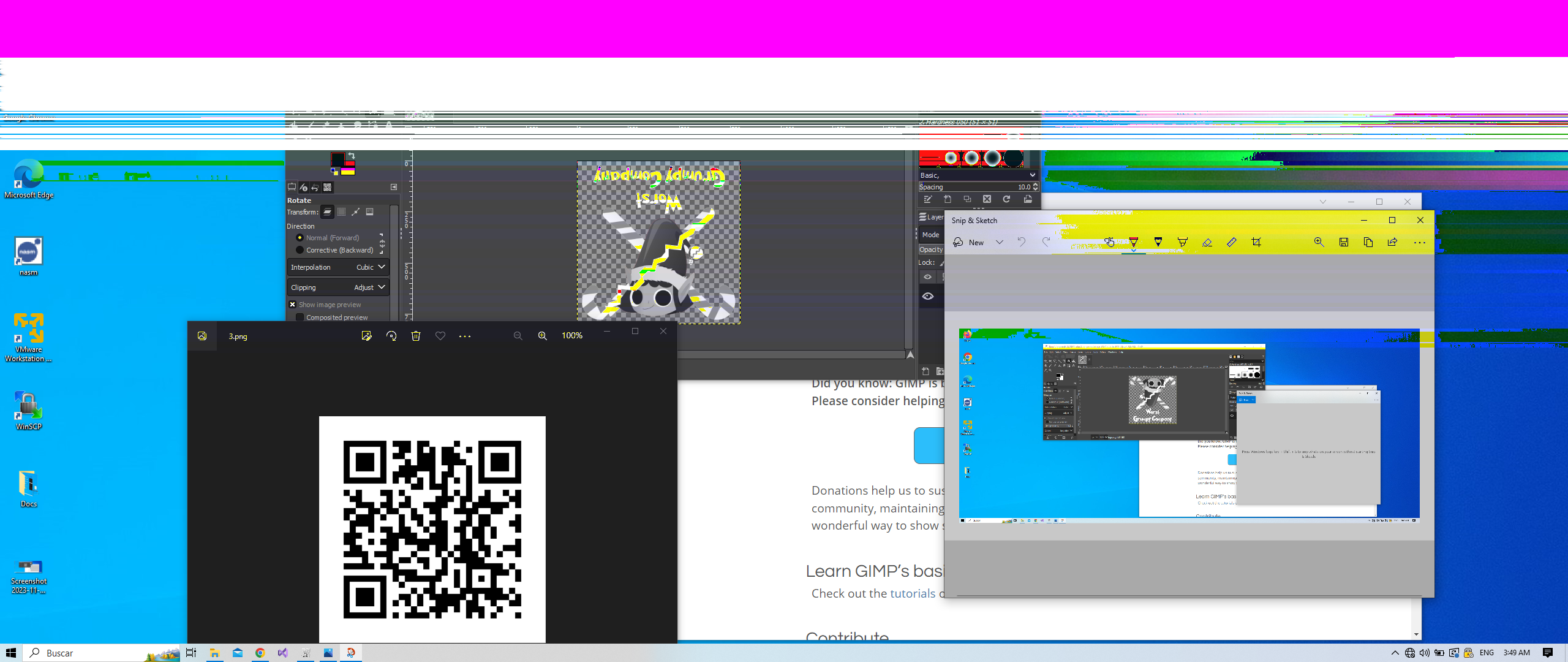
The final URL is https://tryhackme.com/jr/busyvimfrosteau
You can see the write up of this challenge here
Fourth QR Code
At the end of the 20th day we can see:
So we get a look at the GitLab. What I was looking for is a previous commit with the QR Code.
We connect with the given credentials and we go to the project page:
Now we go into the Commit submenu of the Project menu:
As we can see in the commit list, Delf Lead has done a lot of normal commits and then Frostlino came in:
Let’s have a look at the GitLab commit called Updating to this years calendaQR! Meow Meow just before the commit of Frostlino:
We get the QR Code:

The final URL is https://tryhackme.com/jr/surfingyetiiscomingtotown
You can see the write up of this challenge here