WriteUp CTF HackDay : J’ai perdu le flag
We start this challenge with a johnnix folder and a zip johnHacked.zip as shown below.

The zip is protected by a password. So we go to the johnnix folder which contains a lot of text files. The text files don’t seem to be important except for some base64 encoded strings.
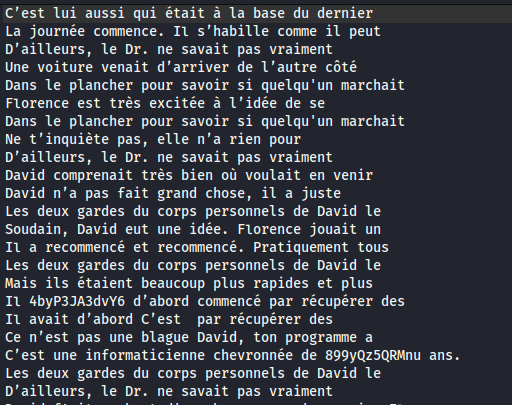
In this folder there is an image of the logo of the event. So we go to aperisolve. We are told that the image contains a Readme file. We extract it with steghide without using passwords.
The text is available here.
I feel like the challenge is in two parts, OSINT and retrieving the words from each file. I start a quick search for this john nix without success. So I create a script to retrieve the first word of line 24 of the following files :
682910xecoz
537w3zly33p
u3ow02q3r77
2i64pvpe639
99u6ov4n2p2
b0448gpzn49
n68ktas0402
fkz90adazd1
The result is as follows:
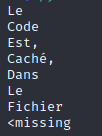
I have the impression that we’ll have to go back to doing OSINT.
At the end of the file, there is the name and surname of the person who wrote the file, but also his email mailto@john.nix@gmx.fr.
So I send an e-mail to dear John and …. gets an automatic answer:
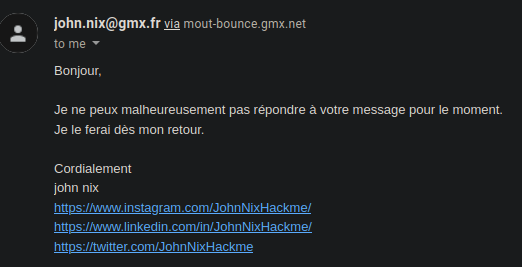
Instagram and LinkedIn links don’t work… But the Twitter does!
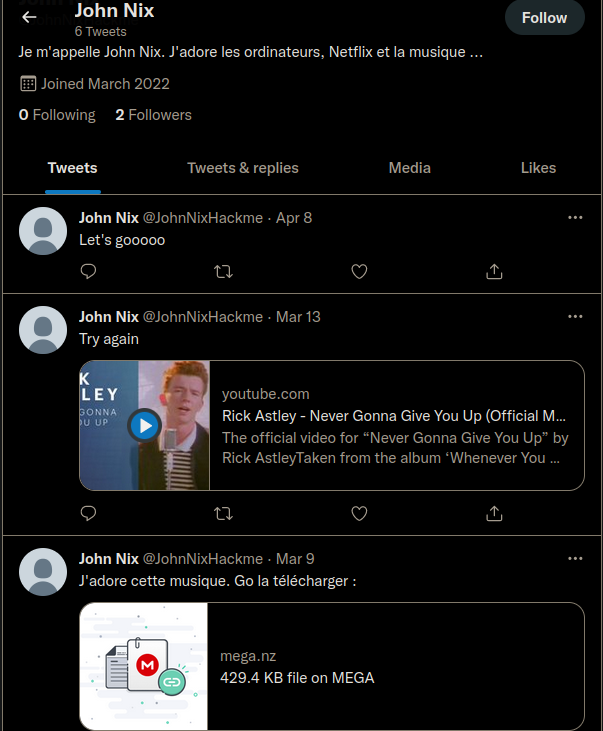
We go to the mega link and download a “.wav” file. My first reflex (after listening to this sweet melodious sound) is to use sonic visualizer which is very useful for audio CTF challenges. We add a spectrogram and … taddaaaaa :

The zip password… or not. In fact, it is the name of a file. We go to the 24th line of the file and the first word is :
For this part the [CyberChef](https://gchq.github.io/CyberChef/) tool can help.
This text is obviously base 64 encoded which gives us once decoded : \
```74 97 68 111 82 101 76 97 83 116 101 103 97 110 111 35 109 108 36 49 36 102 101 56 99 101 55 54 97 53 49```
This new text is obviously base 10 encoded which gives us once decoded : ```JaDoReLaStegano#ml$1$fe8ce76a51```
Bingo the password of the zip!
We unzip it and we get ... 19 new images.
I put the 1st one in aprerisolve and there is a file that can be extracted with steghide without password, same for the 2nd and the 3rd...
I create a script to automate all this and ... back to square one. Texts, an image of Rick and a readme which says to us:
Hey ! Tu y es presque … Encore un peu de recherche :)
🎶 NEVER GONNA GIVE YOU UP 🎶 🎶 NEVER GONNA LET YOU DOWN 🎶 ```
I put the image ImRick.jpg in aperisolve and … it contains another file (fkz90adazd1_) containing the string: fnB0Jnh7Kkx0K3doekllY2JwREhfPUNO
Again base64 which gives us : ~pt&x{*Lt+whzIecbpDH_=CN
The tool dcode can be useful for this part. I try to find the encoding of this string and the ROT47 gives us a rather satisfactory result : OAEUILY{EZH9Kx643Asw0lr}
Well, it’s not the flag but it looks like it.
From there we have two options:
- We have already decoded the base64 strings of the previous files containing the false flags
- We haven’t done it
If we have done it we see that the false flags are of the form HackFlag[xxx]. We test to decode with vigenère and the key HACKFLAG and … END. We have the flag.
Otherwise we can guess it. We test for example the key HACKDAY and we obtain : HACKFLA{XZF9Au643Aup0lp}
From there, either we brute force the key of the form HACK** or we use *HACKFLA and … END… ah no the flag HACKDAY{XZF9As643Psp0lp} does not work. After a little thought we try HACKFLAG and then we have the right flag.