Linux PE (Privilege Escalation)
Exploiting a bug, a design defect, or a configuration oversight in an operating system or software program to acquire elevated access to resources that are typically guarded from an application or user is known as privilege escalation.
As junior pentester we want to become administrator of a machine. We are not going to talk here about CVE (Common Vulnerabilities and Exposures) that are numerous and change depending of the OS, service or method of attack. We are going to talk about basic PE and this list is not exhaustive.
Sudo -l
When we get on a machine we would like to know what rights we have. For that we can type sudo -l. This command will list what we are able to run with the sudo command. The sudo command allow us to execute other commands as another user. The output can look like this:
1
2
User kali may run the following commands on kali:
(ALL : ALL) ALL
This output won’t appear much when you connect on a vulnerable machine but a similar one may. First, what does it mean ? The output is of the form (user:group) command. This output tells us that we can execute any command as any user or group.
The output may more likely look like this :
1
2
User bob may run the following commands on vulnerable:
(root) /usr/bin/find
Note that if the user is different from root, “bob” for example, you can use the
sudocommand like this :sudo -u bob command
Here we see that we can execute the find command as the root user, which is the admin on Linux. You may say “OK, that’s cool but how can the “find” command be useful in PE ?” and you will be right. How can a command that allows us to find files or directories allow us to become root ? Well, there is a wonderful website called GTFOBins where you can find a list of binaries and how to PE with them. If we go here we can see the line that will allow us to become root :
1
sudo find . -exec /bin/sh \; -quit
The PE can be horizontal or vertical. A horizontal PE as its name suggests, is a PE where you stay on the same level. Typically it happens when you change user (not root). And the vertical PE happens when you gain administrator or higher rights.
History
The history can hide sensitive information. We can find credentials, files, command executed… Depending on the shell, you are using the history may have a different name but it will basically be the same name. To know which shall you be using you can type in your terminal echo $SHELL. If you have a zsh shell (the one of kali linux), then your history file is located at ~/.zsh_history. The name will always be .YouShellName_history, so for a bash history it will be located at ~/.bash_history.
SUID
The SUID mean that you can execute a program as the owner (root for example). We can see if a file as the SUID set with ls -l because we will see an “s” instead of the “x” in the rights. We can find all the file with the SUID with the find command :
1
find / -type f -perm -04000 -ls 2>/dev/null
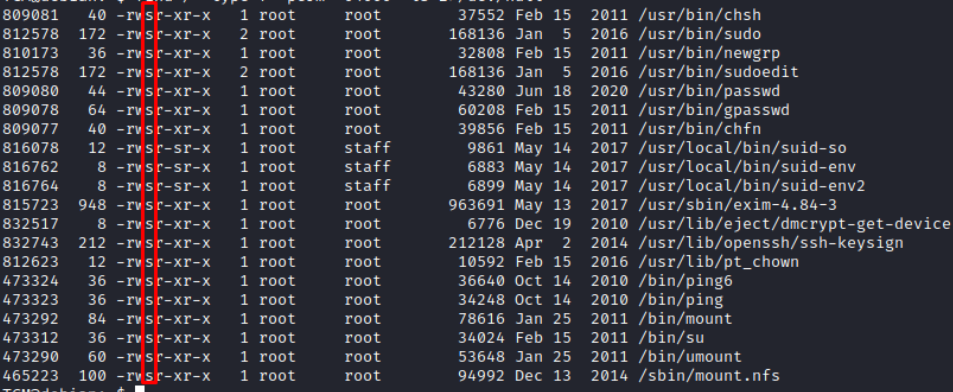
To exploit the SUID we can still use GTFOBins.
Cron
The cron jobs are program that are executed periodically. The cron jobs can be found in the file /etc/crontabs as follows :
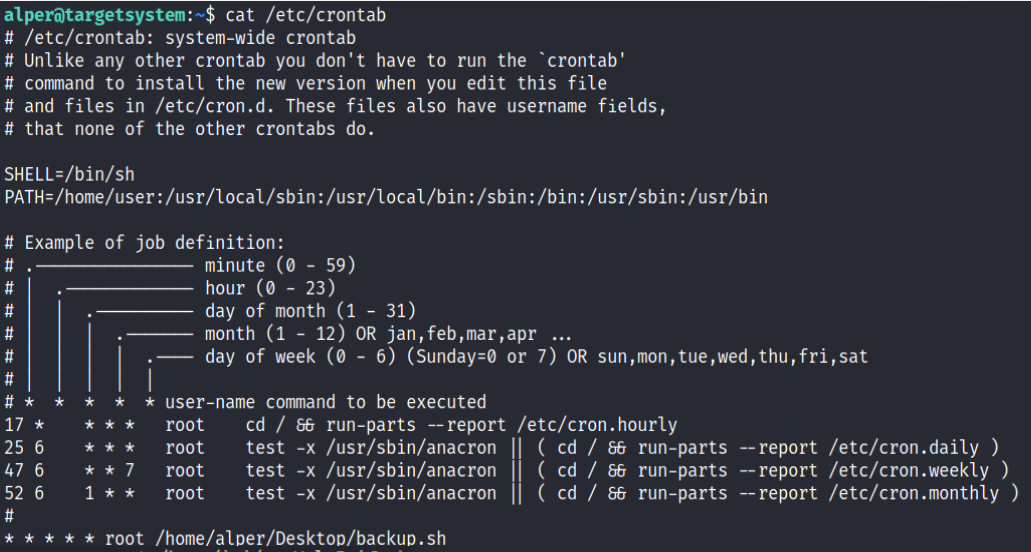
Here we can see an uncommon file called backup.sh on the desktop of the user “alper”. Because there is only stars, it means it is executed every minute. As the image states, the five stars represent respectively minute, hour, day, month and the day of the week when the program is executed.
Linpeas
There are many other vulnerabilities, and we won’t cover them all here. But if you don’t know what to do on a machine or where it can be vulnerable, you can launch linpeas.sh on it. Linpeas is a program that will list CVE, uncommon files in some directories, SUID files and much more. It uses a colour code to tell you if information is relevant or not. As you can see on the screenshot below, we see that things highlight and red have 95% chance to allow us to PE, red things may be interesting…
Exploit DB
If you are looking for an exploit or a specific CVE, there is a good chance the you can find it on the Exploit DB website.
Futher readings
There are many websites that will go into detail about some vulnerabilities like those : HackTricks Hacking Articles …