AutoInfector
When we get to this website we have a button to download a file. If we look at the JS that deals with the action of the button, we get the following code:
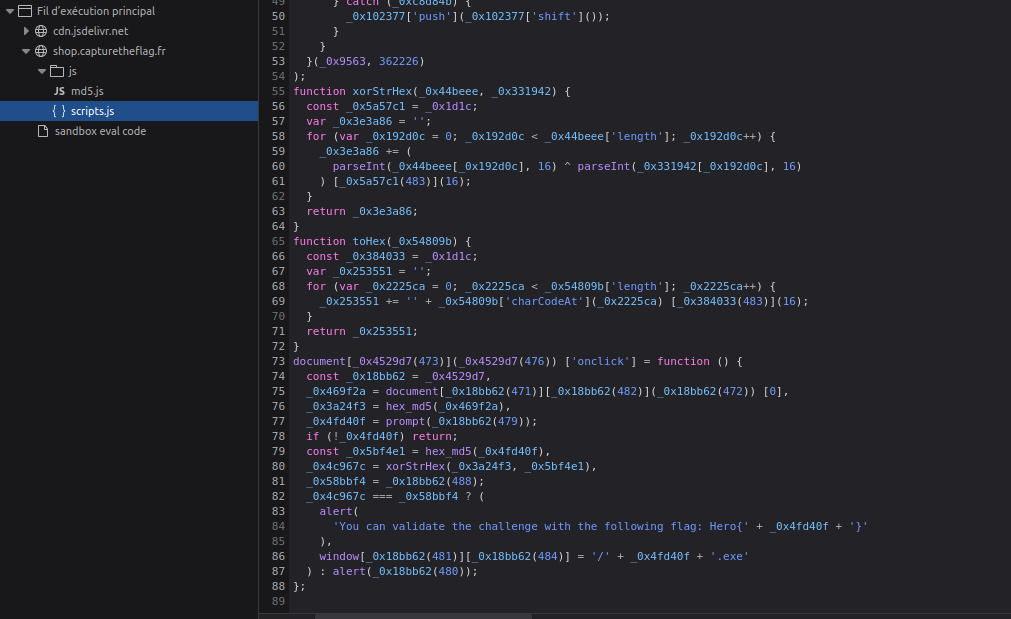
Here is a clearer version of the code:
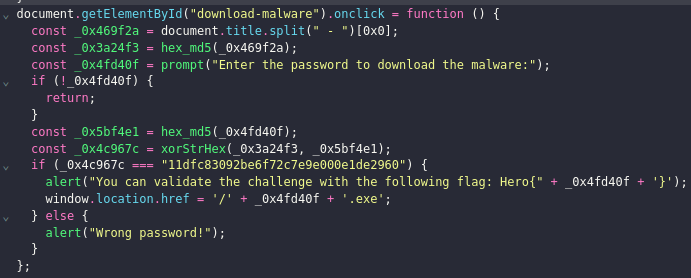
We can use deobfusctor websites like JS Deobfuscator so that we get a better view of the code.
The interesting part starts with the onclick section. Lets break this down line by line:
- First it will get an element from the web page (the title)
- Then it will hash it in
md5(hash1) - After that, it will prompt an input box to allow you to provide the password
- If the provided string isn’t empty, it will hash it in
md5(hash2) - Then it will xor the
hash1withhash2 - If the result is equal to
11dfc83092be6f72c7e9e000e1de2960(hash3) then it will prompt the flag
So basically we have: hash3 = hash1 XOR hash2
We know hash3 and hash1. The only thing we don’t know is hash2 because it depends on what we input. So if we do a XOR operation between the two known hash, we should get the hash we don’t know (basic XOR rule). So we can do the following:
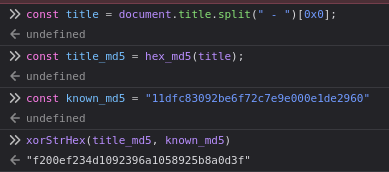
Now that we have the hash we can crack it using hashcat:
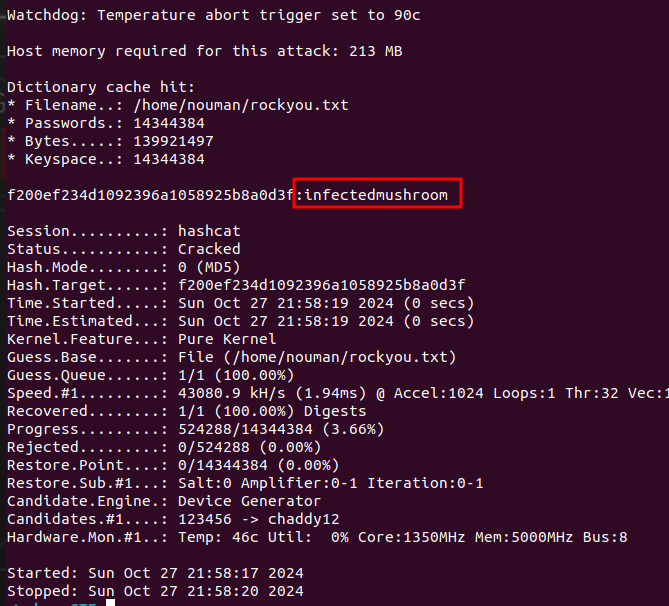
The full
hashcatcommand is justhashcat -m 0 known_hash ~/rockyou.txt
And now we can use this as the password to get the flag. And.. Voila: