Lettres volatiles
In this challenge we are given a Windows home directory of the user C311M1N1. When looking around, we can find a zip file containing a pdf that is protected by a password:
This may be where the flag is hidden. We can try to find the password now. In the directory Documents/JumpBag/ we find a raw file that we can analyse using Volatility. In this particular case, we need to use volatility2. We first need to find the correct profile:
Here is a, non complete, but still useful cheat-sheet about basic command in
Volatiltiy2and their equivalent inVolatiltiy3
Now that we have the correct profil, we can execute any command we want. I tried looking a process running, on the network, at process to dump… But didn’t find anything interesting. I then found the command clipboard that allows us to get the content of the clipboard and…
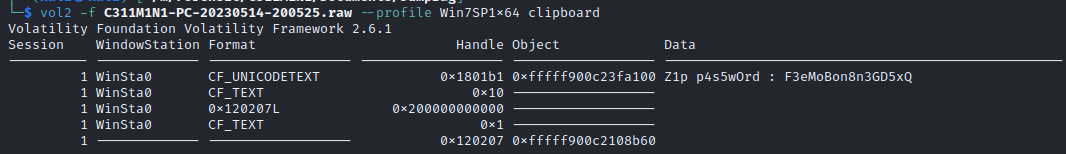
We then use the password F3eMoBon8n3GD5xQ on the s3cR37.zip file and… Voilà:
When we open the PDF file we get:

The flag is 404CTF{V0147i1I7y_W1Ll_N3v3r_Wr8_loV3_l3ttEr5}